Software Management profiles
NAVIGATION Software Management > Profiles > Scan and Analysis > New/Edit
The Scan and Analysis page creates profiles that specify the patch strategy used to select patches for deployment. A Scan and Analysis profile also specifies when a scan runs on a recurring schedule. A scan can always be run immediately using the Scan Now button on the Machines page.
Patch strategies
A Scan and Analysis profile specifies one of three patch strategies to select and deploy patches:
Actions
- New: Creates a Scan and Analysis profile using one of two patch strategies.
- Profile Name
- OS Patches Impact Rules: By default, Kaseya 2.0 is selected.
- OS Patches Engine
- Critical
- Approve
- Suppress
- Reject
- Review
- Critical, Older than 30 days
- Approve
- Suppress
- Reject
- Review
- Recommended
- Approve
- Suppress
- Reject
- Review
- Virus Removal
- Approve
- Suppress
- Reject
- Review
- Critical
- 3rd-Party Software Patches Rules
- Procedures
- Pre-Scan Procedure
- Post Scan Procedure
- Scan Schedule
- Time Frame
- Daily
- Weekly
- Monthly
- Run Time: Agent time
- Distribution Window
- Time Frame
- Execution Options
- Skip If Offline
- Power up if offline
NOTE Requires Wake-On-LAN or vPro and another managed system on the system LAN.
- File Source
- Internet
- VSA Server
- Lan Cache
NOTE Only available for OS Native and Kaseya 2.0 OS Patches engines.
NOTE When the patch strategy is changed to the deprecated value, the error message displayed is Warning. It is not recommended to use selected OS Patches Engine, it is marked as deprecated.
You can also edit a profile, delete a profile, or refresh the grid.
Machines Assigned
Machines can also be assigned profiles:
- Assign: Assigns selected machines to a profile. A machine can only be assigned one profile at a time.
- Remove: Removes selected machines from a profile.
Patch strategy configurations
NAVIGATION Software Management > Profiles > Scan and Analysis
The Configure Operating System Update strategy configures how updates for Windows and macOS machines are performed on assigned machines. Individual Windows and macOS patches are not reviewed and selected using this option. Third-party patches cannot be deployed using this strategy.
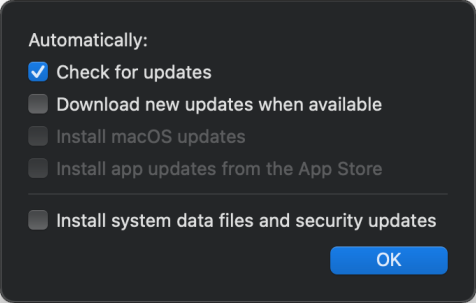
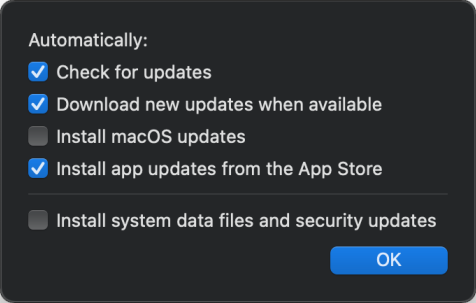
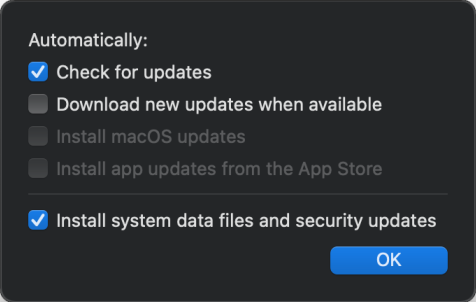
Operating system update
- Ask user to download and install
- Automatically download and ask user to install
- Automatically download and schedule installation
- Require automatic updates but let user configure
- Turn off Operating System Update
Schedule options
- Schedule on Every Day, Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, Saturday at <time>
- Reboot
- Forced reboot if user is logged in
- Do not force reboot
NAVIGATION Software Management > Profiles > Scan and Analysis
The Only OS Updates patch strategy configures how updates for Windows and Apple machines are performed on assigned machines.
Individual Windows and Apple patches are not reviewed and selected using this option.
Third-party patches cannot be deployed using this strategy. Use the Third Party Software Updates + OS Updates strategy if you want to configure third-party software updates, as well.
Using this strategy takes effect as soon as the machine is assigned to the profile, wherever the profile is updated.
When this patch strategy is selected, two sections appear:
- Configure Windows Group Policies Related to Windows Update
- macOS Update Settings
Configuring Windows Group Policies Related to Windows Update
This section contains all Windows group policies related to Windows updates. They can be configured in VSA in a similar way to what an administrator would do on a domain controller if their organization uses Active Directory.
This policy can have the following statuses:
- Enabled: Windows behaves in the way specified by the policy, and it uses the specified options. The endpoint user is not able to modify those settings in the Windows Update application.
- Disabled: The policy is turned off, and the endpoint user is not able to modify those settings in the Windows Update application.
- Not Configured: The policy is turned off, but endpoint user is able to modify those settings in the Windows Update application.
Some policies contain variables and/or values required, such as (but not limited to) hours, minutes, or days.
After unassigning a machine from the profile, all policies are set back to the Not Configured status (default Windows configuration).
Windows policies configured in this section are applied on a machine level. If an endpoint user configured any of the policies listed in this section, their configuration will be overridden when the Scan and Analysis profile is applied. However, this configuration has lower priority than Windows policies configured by an administrator on a domain controller (in case their organization uses Active Directory).
To understand the Native Windows Patching Controls Configuration from Microsoft, refer to this Microsoft article.
This policy specifies whether the computer will receive security updates and other important downloads through the Windows automatic updating service.
NOTE This policy does not apply to Windows RT.
This policy can have the following statuses:
- Enabled: This option specifies that local administrators will be allowed to use the Windows Update control panel to select a configuration option of their choice. However, local administrators will not be allowed to disable the configuration for Automatic Updates.
- Disabled: If this option is selected, any updates that are available on Windows Update must be downloaded and installed manually. To do this, search for Windows Update using Start.
- Not Configured: If this option is selected, use of Automatic Updates is not specified at the Group Policy level. However, an administrator can still configure Automatic Updates through Control Panel.
This policy specifies whether Automatic Updates will deliver both important as well as recommended updates from the Windows Update service.
This policy can have the following statuses:
- Enabled: If this option is selected, Automatic Updates will install recommended updates as well as important updates from Windows Update service.
- Disabled: If this option is selected, Automatic Updates will continue to deliver important updates if it is already configured to do so.
- Not Configured: If this option is selected, Automatic Updates will continue to deliver important updates if it is already configured to do so.
This policy specifies the hours that Windows will use to determine how long to wait before checking for available updates.
NOTE The Specify intranet Microsoft update service location setting must be enabled for this policy to have effect. If the Configure Automatic Updates policy is disabled, this policy has no effect. This policy is not supported on Windows RT. Setting this policy will not have any effect on Windows RT PCs.
This policy can have the following statuses:
- Enabled: If this option is selected, Windows will check for available updates at the specified interval.
- Interval (hours): The exact wait time is a sum of the specific value and a random variant of 0-4 hours.
- Disabled: If this option is selected, Windows will check for available updates at the default interval of 22 hours.
- Not Configured: If this option is selected, Windows will check for available updates at the default interval of 22 hours.
This policy specifies whether Automatic Updates should automatically install certain updates that neither interrupt Windows services nor restart Windows.
NOTE If the Configure Automatic Updates policy is disabled, this policy has no effect.
This policy can have the following statuses:
- Enabled: If this option is selected, Automatic Updates will immediately install these updates once they are downloaded and ready to install.
- Disabled: If this option is selected, Automatic Updates will not be installed immediately.
- Not Configured: If this option is selected, Automatic Updates will not be installed immediately.
This policy specifies whether Automatic Updates accepts updates signed by entities other than Microsoft when the update is found on an intranet Microsoft update service location.
NOTE Updates from a service other than an intranet Microsoft update service must always be signed by Microsoft and are not affected by this policy setting. This policy is not supported on Windows RT. Setting this policy will not have any effect on Windows RT PCs.
This policy can have the following statuses:
- Enabled: If this option is selected, Automatic Updates accepts updates received through an intranet Microsoft update service location if they are signed by a certificate found in the Trusted Publishers certificate store of the local computer.
- Disabled: If this option is selected, Automatic Updates from an intranet Microsoft update service location must be signed by Microsoft.
- Not Configured: If this option is selected, Automatic Updates from an intranet Microsoft update service location must be signed by Microsoft.
This policy specifies the amount of time Automatic Updates will wait before proceeding with a scheduled restart.
NOTE This policy applies only when Automatic Updates is configured to perform scheduled installations of updates. If the Configure Automatic Updates policy is disabled, this policy has no effect.
This policy can have the following statuses:
- Enabled: If this option is selected, a scheduled restart will occur after the specified number of minutes has expired.
- Restart (minutes): Specifies the amount of time (in minutes) Automatic Updates waits before proceeding with a scheduled restart.
- Disabled: If this option is selected, the default wait time of 15 minutes will elapse before any scheduled restart occurs.
- Not Configured: If this option is selected, the default wait time of 15 minutes will elapse before any scheduled restart occurs.
This policy specifies whether Windows Update will use the Windows Power Management features to automatically wake up the system from hibernation if updates are scheduled for installation.
This policy can have the following statuses:
- Enabled: If this option is selected, Windows Update will automatically wake up the system only if Windows Update is configured to install updates automatically. If the system is in hibernation when the scheduled install time occurs and updates are available to be applied, then Windows Update will use the Windows Power management features to automatically wake the system up to install the updates.
- Disabled: If this option is selected, the system will not wake unless there are updates to be installed. If the system is on battery power, when Windows Update wakes it up, it will not install updates and the system will automatically return to hibernation in two minutes.
- Not Configured: If this option is selected, Windows Update does not wake the computer from hibernation to install updates.
This policy specifies that to complete a scheduled installation, Automatic Updates will wait for the computer to be restarted by any user who is logged on instead of causing the computer to restart automatically.
NOTE This policy applies only when Automatic Updates is configured to perform scheduled installations of updates. If the Configure Automatic Updates policy is disabled, this policy has no effect.
This policy can have the following statuses:
- Enabled: If this option is selected, Automatic Updates will not restart a computer automatically during a scheduled installation if a user is logged in to the computer. Instead, Automatic Updates will notify the user to restart the computer.
- Disabled: If this option is selected, Automatic Updates will notify the user that the computer will automatically restart in five minutes to complete the installation.
- Not Configured: If this option is selected, Automatic Updates will notify the user that the computer will automatically restart in five minutes to complete the installation.
NOTE The computer needs to be restarted for the updates to take effect.
This policy specifies the amount of time for Automatic Updates to wait before prompting again with a scheduled restart.
NOTE This policy applies only when Automatic Updates is configured to perform scheduled installations of updates. If the Configure Automatic Updates policy is disabled, this policy has no effect. This policy has no effect on Windows RT.
This policy can have the following statuses:
- Enabled: If this option is selected, a scheduled restart will occur the specified number of minutes after the previous prompt for restart was postponed.
- Restart (minutes): Specifies the number of minutes after the previous prompt.
- Disabled: If this option is selected, the default interval is 10 minutes.
- Not Configured: If this option is selected, the default interval is 10 minutes.
This policy allows you to manage whether the Install Updates and Shut Down option is displayed in the Shut Down Windows dialog box.
This policy can have the following statuses:
- Enabled: If this option is selected, Install Updates and Shut Down will not appear as a choice in the Shut Down Windows dialog box, even if updates are available for installation when the user selects the Shut Down option in the Start menu.
- Disabled: If this option is selected, the Install Updates and Shut Down option will be available in the Shut Down Windows dialog box if updates are available when the user selects the Shut Down option in the Start menu.
- Not Configured: If this option is selected, the Install Updates and Shut Down option will be available in the Shut Down Windows dialog box if updates are available when the user selects the Shut Down option in the Start menu.
This policy allows you to manage whether the Install Updates and Shut Down option is allowed to be the default choice in the Shut Down Windows dialog box.
This policy setting has no impact if the Computer Configuration\Administrative Templates\Windows Components\Windows Update\Do not display 'Install Updates and Shut Down' option in Shut Down Windows dialog box policy setting is enabled.
This policy can have the following statuses:
- Enabled: If this option is selected, the user's last shut down choice (Hibernate, Restart, and so forth) is the default option in the Shut Down Windows dialog box regardless of whether the Install Updates and Shut Down option is available in the What do you want the computer to do? list.
- Disabled: If this option is selected, the Install Updates and Shut Down option will be the default option in the Shut Down Windows dialog box if updates are available for installation at the time the user selects the Shut Down option in the Start menu.
- Not Configured: If this option is selected, the Install Updates and Shut Down option will be the default option in the Shut Down Windows dialog box if updates are available for installation at the time the user selects the Shut Down option in the Start menu.
This policy allows you to control whether users see detailed enhanced notification messages about featured software from the Microsoft Update service. Enhanced notification messages convey the value and promote the installation and use of optional software. This policy setting is intended for use in loosely managed environments in which you allow the end user access to the Microsoft Update service.
By default, this policy setting is disabled. If you are not using the Microsoft Update service, then the Turn on Software Notifications policy setting has no effect. If the Configure Automatic Updates policy setting is disabled or is not configured, then the Turn on Software Notifications policy setting has no effect.
This policy can have the following statuses:
- Enabled: If this option is selected, a notification message will appear on the user's computer when featured software is available. The user can click the notification to open the Windows Update application and get more information about the software or install it. The user can also click Close this message or Show me later to defer the notification as appropriate.
- Disabled: If this option is selected, Windows 7 users will not be offered detailed notification messages for optional applications, and Windows Vista users will not be offered detailed notification messages for optional applications or updates.
- Not Configured: If this option is selected, Windows 7 users will not be offered detailed notification messages for optional applications, and Windows Vista users will not be offered detailed notification messages for optional applications or updates.
This policy specifies a restart timer always begins immediately after Windows Update installs important updates instead of first notifying users on the login screen for at least two days.
NOTE If the No auto-restart with logged on users for scheduled automatic updates installations policy is enabled, then this policy has no effect.
This policy can have the following statuses:
- Enabled: If this option is selected, a restart timer will always begin immediately after Windows Update installs important updates instead of first notifying users on the login screen for at least two days.
- Work (minutes): Configures the restart timer to start with any value from 15 to 180 minutes. When the timer runs out, the restart will proceed even if the PC has signed-in users.
- Disabled: If this option is selected, Windows Update will not alter its restart behavior.
- Not Configured: If this option is selected, Windows Update will not alter its restart behavior.
This policy specifies to not retrieve information from the public Windows Update service to enable future connections to Windows Update, and other services like Microsoft Update or the Windows Store, when Windows Update is configured to receive updates from an intranet update service.
NOTE This policy applies only when this PC is configured to connect to an intranet update service using the Specify intranet Microsoft update service location policy.
This policy can have the following statuses:
- Enabled: If this option is selected, it will disable functionality to retrieve information from the public Windows Update service and may cause connection to public services such as the Windows Store to stop working.
- Disabled: If this option is selected, it will not disable functionality to retrieve information from the public Windows Update service.
- Not Configured: If this option is selected, it will not disable functionality to retrieve information from the public Windows Update service.
This policy specifies the level of Preview Build or Feature Updates to receive.
This policy can have the following statuses:
- Enabled: If this option is selected, it specifies the level of Preview Build or Feature Updates to receive, and when.
- Preview Build - Fast: Devices set to this level will be the first to receive new builds of Windows with features not yet available to the general public. Select Fast to participate in identifying and reporting issues to Microsoft and provide suggestions on new functionality.
- Preview Build - Slow: Devices set to this level receive new builds of Windows before they are available to the general public, but at a slower cadence than those set to Fast, and with changes and fixes identified in earlier builds.
- Release Preview: Receive builds of Windows just before Microsoft releases them to the general public.
- Semi-Annual Channel (Targeted): Receive feature updates when they are released to the general public.
- Semi-Annual Channel: Feature updates will arrive when they are declared Semi-Annual Channel. This usually occurs about 4 months after Semi-Annual Channel (Targeted), indicating that Microsoft, Independent Software Vendors (ISVs), partners, and customers believe that the release is ready for broad deployment.
- After a Preview Build or Feature Update is released, defer receiving it for this many days: You can defer receiving preview builds for up to 14 days.
-
Pause Preview Builds or Feature Updates starting (yyyy-mm-dd): To prevent preview builds from being received on their scheduled time, you can temporarily pause them. The pause will remain in effect for 35 days from the start time provided. To resume receiving feature updates that are paused, clear the start date field.
- Disabled: If this option is selected, Windows Update will not alter policy behavior.
- Not Configured: If this option is selected, Windows Update will not alter policy behavior.
Select the Windows readiness level for the updates you want to receive:
This policy specifies when to received Quality Updates.
NOTE If the Allow Telemetry policy is set to 0, this policy will have no effect.
This policy can have the following statuses:
- Enabled: If this option is selected, specifies when to receive quality updates.
- After a quality update is released, defer receiving it for this many days: You can defer receiving quality updates for up to 30 days.
- Pause Quality Updates starting: To prevent quality updates from being received on their scheduled time, you can temporarily pause quality updates. The pause will remain in effect for 35 days or until you clear the start date field.
- Disabled: If this option is selected, Windows Update will not alter policy behavior.
- Not Configured: If this option is selected, Windows Update will not alter policy behavior.
This policy specifies whether or not to download updates automatically even over metered data connections.
This policy can have the following statuses:
- Enabled: If this option is selected, the updates will be automatically downloaded, even over metered data connections.
- Disabled: If this option is selected, the updates will not be automatically downloaded.
- Not Configured: If this option is selected, the updates will not be automatically downloaded.
This policy specifies the PC not to restart automatically after updates during active hours. If any of the following two policies are enabled, this policy has no effect:
- No auto-restart with logged on users for scheduled automatic updates installations.
- Always automatically restart at scheduled time.
This policy can have the following statuses:
- Enabled: If this option is selected, the PC will not automatically restart after updates during active hours. The PC will attempt to restart outside of active hours.
- Start: Specifies the start time for updates.
- End: Specifies the end time for updates.
- Disabled: If this option is selected, the user selected active hours will be in effect.
- Not Configured: If this option is selected, the user selected active hours will be in effect.
NOTE The default max active hours range is 18 hours from the active hours start time unless otherwise configured via the Specify active hours range for auto-restart policy.
This policy specifies an intranet server to host updates from Microsoft Update. You can then use this update service to automatically update computers on your network.
NOTE If the Configure Automatic Updates policy is disabled, then this policy has no effect. If the Alternate Download Server is not set, it will use the intranet update service by default to download updates.
This policy can have the following statuses:
- Enabled: If this option is selected, the Automatic Updates client connects to the specified intranet Microsoft update service (or alternate download server), instead of Windows Update, to search for and download updates.
- Set the intranet update service for detecting updates: Specifies a server on your network to function as an internal update service. The Automatic Updates client will search this service for updates that apply to the computers on your network.
- Set the intranet statistics server: Specifies a server on your network to function as an intranet statistics server.
- Set the alternate download server: Specifies the Windows Update Agent to download files from an alternative download server instead of the intranet update service.
- Download files with no Url in the metadata if alternate download server is set: Allows content to be downloaded from the Alternate Download Server when there are no download URLs for files in the update metadata. This option should only be used when the intranet update service does not provide download URLs in the update metadata for files which are present on the alternate download server. This option is only used if the Alternate Download Server is set.
- Disabled: If this option is selected, and if Automatic Updates is not disabled by policy or user preference, the Automatic Updates client connects directly to the Windows Update site on the internet.
- Not Configured: If this option is selected, and if Automatic Updates is not disabled by policy or user preference, the Automatic Updates client connects directly to the Windows Update site on the internet.
This policy specifies when auto-restart reminders are displayed.
This policy can have the following statuses:
- Enabled: If this option is selected, you must specify the period to notify the user.
- Period (min): Specifies the amount of time prior to a scheduled restart to notify the user.
- Disabled: If this option is selected, the default period will be used.
- Not Configured: If this option is selected, the default period will be used.
This policy specifies the method by which the auto-restart required notification is dismissed.
This policy can have the following statuses:
- Enabled: If this option is selected, you must specify method by which the auto-restart required notification is dismissed. When a restart is required to install updates, the auto-restart required notification is displayed. By default, the notification is automatically dismissed after 25 seconds.
- Method: Must be set to require user action to dismiss the notification.
- Disabled: If this option is selected, the default method will be used.
- Not Configured: If this option is selected, the default method will be used.
This policy allows to control when notifications are displayed to warn users about a scheduled restart for the update installation deadline.
This policy can have the following statuses:
- Enabled: If this option is selected, notifications are displayed to warn users about a scheduled restart for the update installation deadline. Users are not able to postpone the scheduled restart once the deadline has been reached and the restart is automatically executed.
- Reminder (hours): Specifies the amount of time prior to a scheduled restart to display the warning reminder to the user.
- Warning (mins): The amount of time prior to a scheduled restart to notify the user that the auto-restart is imminent to allow them time to save their work.
- Disabled: If this option is selected, the default notification behaviors will be used.
- Not Configured: If this option is selected, the default notification behaviors will be used.
This policy specifies the maximum background download bandwidth that Delivery Optimization uses across all concurrent download activities as a percentage of available download bandwidth.
This policy can have the following statuses:
- Enabled: If this option is selected, the maximum background download bandwidth that Delivery Optimization uses across all concurrent download activities as a percentage of available download bandwidth.
- Maximum Background Download Bandwidth (percentage): The default value 0 means that Delivery Optimization dynamically adjusts to use the available bandwidth for background downloads.
- Disabled: If this option is selected, the maximum background download bandwidth that Delivery Optimization does not use across all concurrent download activities as a percentage of available download bandwidth.
- Not Configured: If this option is selected, the maximum background download bandwidth that Delivery Optimization does not use across all concurrent download activities as a percentage of available download bandwidth.
This policy specifies the maximum foreground download bandwidth that Delivery Optimization uses across all concurrent download activities as a percentage of available download bandwidth.
This policy can have the following statuses:
- Enabled: If this option is selected, the maximum background download bandwidth that Delivery Optimization uses across all concurrent download activities as a percentage of available download bandwidth.
- Maximum Foreground Download Bandwidth (percentage): The default value 0 means that Delivery Optimization dynamically adjusts to use the available bandwidth for foreground downloads.
- Disabled: If this option is selected, the maximum background download bandwidth that Delivery Optimization does not use across all concurrent download activities as a percentage of available download bandwidth.
- Not Configured: If this option is selected, the maximum background download bandwidth that Delivery Optimization does not use across all concurrent download activities as a percentage of available download bandwidth.
macOS Update Settings
The following macOS settings are selected in the System Preferences > Apple Store dialog for each Operating System Update value selected in Software Management.
Mapping to macOS Software Update
NOTE macOS Software Update settings options should be deployed during the machine scan process.
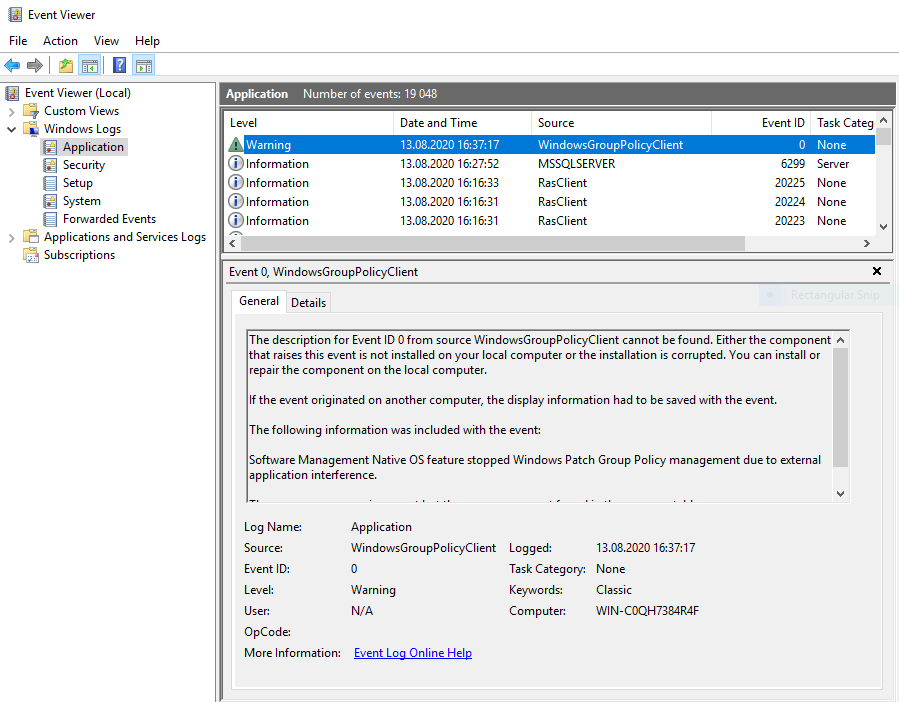
Windows Native Patching Monitoring
This feature can work only if no other applications are aggressively trying to change the Windows Update GPO. In case there is such an application, the feature will stop trying to enforce its configuration and log the following log to the Windows Event Log:
Software Management Native OS feature stopped Windows Patch Group Policy management due to external application interference."
NOTE Once the log problem is fixed, the machine needs to be restarted or the profile reapplied from the VSA.
The Software Management Native OS feature will stop applying the configuration and write the warning if more than 20 changes occur in the OS patching GPOs within one hour.
NAVIGATION Software Management > Profiles > Scan and Analysis
This patch strategy configures how updates for Windows and Apple machines are performed on assigned machines. Additionally, it allows use of third-party Software Management.
All agents assigned a Scan and Analysis profile using the Third-Party Software Updates + OS Updates patch strategy must have a Deployment profile assigned to them or third-party software patches will not be deployed.
The schedule section governs only scans of third-party software. It is not related to OS updates configuration defined in next sections, which are applied immediately. At the times specified in the schedule, every endpoint assigned to the profile is scanned. The scan checks if software defined in the 3rd-Party Software profile is installed and up to date.
OS updates configuration sections are described in detail in Only OS Updates.
NAVIGATION Software Management > Profiles > Scan and Analysis
A profile using the Kaseya Update patch strategy specifies whether to approve, reject, or review patches using a preassigned impact classification. Reviewed and rejected patches can be subsequently approved using either the Patch Approval page or the Machines page.
All agents assigned a Scan and Analysis profile using the Kaseya Update patch strategy must have a Deployment profile assigned to them or patches will not be deployed.
This patch strategy applies to Microsoft, Apple, and third-party software title patches.
When this patch strategy is selected, the following additional options appear:
- Patch Impact: Sets the criteria to Approve, Suppress, Review, or Reject patches by patch impact classification.
- Critical
- Critical, Older than 30 Days
- Recommended
- Virus Removal
- Schedule
- Time Frame:
- If Daily is selected, Run Every X Days is displayed. Enter the interval of days run.
- If Weekly is selected, Sunday through Saturday is displayed. Select the days of the week to run.
- If Monthly is selected, Run Every X Months is displayed. Enter additional parameters to specify the interval of months to run and when to run during a month.
- Scan Run Time (agent time): Enter the agent time to run.
- Distribution Window
- Skip if Offline
- Power up if Offline
- Time Frame:
The following options select an agent procedure to run before or after scan:
- Pre-Scan Procedure
- Post-Scan Procedure
NAVIGATION Software Management > Profiles > Override
The Override page specifies named sets of selected overrides. An override exists for each patch that can be deployed. These overrides, if assigned to a machine, take precedence over the approval, review, or rejection of these same patches assigned to a machine by the Scan and Analysis or 3rd-Party Software profile. Overrides are assigned to machines using the Assign Profiles button on the Machines page.
Overrides have precedence from highest to lowest in each override list. On the Override page, you can reorder overrides by dragging and dropping them within a list during editing. Once an override list is assigned to a machine on the Machines page, you can adjust the order of overrides for each machine separately or delete an override for an individual machine.
NOTE When override profile is created and assigned to endpoint, a scan is required to implement override attributes.
You can specify overrides using three tabs:
IMPORTANT The KB and patch override function(s) will be deprecated only when new engines are released. You may continue to utilize this today with Software Management however, we strongly encourage you to begin your override migrations into the Overrides tab to ensure no interruption to your rules in the near future.
Overrides tab (formerly Advanced Override)
This functionality supports KB and patch overrides. Override profiles support 3rd-Party Software Patches in their rules.
Specifies overrides using custom filtering.
- New: Opens a dialog to specify a patch override profile by custom filtering.
- Name: The name of the override profile.
- Add Row: Adds a new row. For a row, enter values for the following:
- Approve/Reject: Select Approve, Reject, or Review.
- Field:
- CVE Code: Refers to a Common Vulnerabilities and Exposures identifier for a patch.
- Name
- Description
- Vendor
- Product
- Release Date
- KB#
- MS Security ID
- Operator: Like matches if the value entered is contained in the field.
- Equals
- Not equal to
- Contains
- Does not contain
- Value: Enter any string to filter by.
- Delete Row: Deletes a selected row.
- Edit: Edit an existing override profile.
- Delete: Deletes an override profile.
KB Override tab
Specifies overrides for patches identified by Microsoft KB number.
- New: Opens a dialog to specify a KB patch override profile.
- Name: The name of the override profile.
- Add Row: Adds a new row. For a row, select Approve, Reject, or Review. Then, select the KB patch.
- Delete Row: Deletes a selected row.
- Edit: Edit an existing override profile.
- Delete: Deletes an override profile.
Patch Override tab
Specifies overrides for patches not identified by Microsoft KB number.
- New: Opens a dialog to specify a patch override profile.
- Name: The name of the override profile.
- Add Row: Adds a new row. For a row, select Approve, Reject, or Review. Then, select the KB patch.
- Delete Row: Deletes a selected row.
- Edit: Edit an existing override profile.
- Delete: Deletes an override profile.
NAVIGATION Software Management > Profiles > 3rd-Party Software 1.0
The 3rd-Party Software page assigns software titles, by version number, to a profile. 3rd-Party Software profiles are then assigned to machines using either this page or the Assign Profiles button on the Machines page. Software titles are deployed based on the schedule specified by a machine's assigned Deployment profile. 3rd party software cannot be deployed on demand.
Column K3PP on the 3rd-Party Software 1.0 page is removed. The profiles list on this page is filtered to show only profiles of type Kaseya 1.0.
Actions
- New: Opens a profile dialog that specifies a list of software titles by vendor, title, and version.
- Name
- Description
- Software Titles: Search for and add software titles and versions. You cannot add two versions of the same software title to the profile.
- Add Multiple Titles: Adds third--party multiple titles from the list.
- Add Individual Titles: Adds third-party individual titles from the drop-down.
- Delete: Deletes a software title and version from the profile.
- Add: Opens a dialog to search for and add software titles and versions. You cannot add two versions of the same software title to the profile.
- Delete: Deletes a software title and version from the profile.
- Edit: Edits an existing profile.
- Delete: Deletes a profile.
- Refresh: Refreshes the grid.
Machines Assigned
- Assign: Assigns selected machines to a profile. A machine can only be assigned one profile at a time.
- Remove: Removes selected machines from a profile.
NAVIGATION Software Management > Profiles > Deployment
The Deployment page creates profiles that specify how and when deployments are executed on assigned machines. This profile can be assigned on this page or on the Machines page.
Actions
- New: Creates a Deployment profile.
- Edit: Edit a selected profile.
- Delete: Deletes the selected profile.
- Refresh: Refreshes the grid.
Machines Assigned
Machines can also be assigned profiles using the Machines page.
- Assign: Assigns selected machines to a profile. A machine can only be assigned one profile at a time.
- Remove: Removes selected machines from a profile.
Deployment profile options
Reboot Options
Reboot prompts and warnings occur after the install.
- When the user is logged in
- Reboot immediately after update
- Ask user about reboot and offer to delay (reask every x minute); do not reboot until get response
- Ask permission, if no response in x min reboot
- Skip Reboot
- Do not reboot after update, send email
NOTE You can configure the email format using the Settings page.
- Wait time: Minutes to wait after warning the user of reboot.
- When a user is not logged in
- Reboot immediately after update
- Warn user and wait for x min and then reboot
- Skip Reboot
- Do not reboot after update, send email
NOTE You can configure the email format using the Settings page.
NOTE If patch deployments configured with Reboot immediately after update complete within a blackout window, the reboot may be suspended until the until the end of the blackout window. See the Blackout Window section below for further details.
Procedures
The following options select an agent procedure to run before or after an update or reboot:
- Pre-Update Procedure
- Pre-Reboot Procedure
- Post-Update Procedure
- Post-Reboot Procedure
NOTE Pre-reboot procedures will be honored even when reboot is not initiated by patch or profile.
Schedule
Schedules recurring deployments. The recurring schedule for a deployment typically follows the recurring schedule for a Scan and Analysis scan by at least several hours.
- Time Frame:
- If Daily is selected, Run Every X Days is displayed. Enter the interval of days run.
- If Weekly is selected, Sunday through Saturday is displayed. Select the days of the week to run.
- If Monthly is selected, Run Every X Months is displayed. Enter additional parameters to specify the interval of months to run and when to run during a month.
- Run Time: Enter the agent time to run.
- Distribution Window
- Skip if Offline
- Power up if Offline
Blackout Window
Blackout windows prevent schedule deployments from being run during specified days/times of the week. A scheduled run time can only be specified outside of a blackout window.
NOTE If an in-progress patch deployment configured to Reboot immediately after update completes during a blackout window with a defined End Time, the reboot will be postponed until the end of the blackout window. If the blackout window's End Time is set to Do not restart until the next profile time, the reboot will happen immediately after deployment, overriding the blackout window.
- Start Day, End Day: Select day from Sunday to Saturday, or choose Every Day.
- Start Time: Choose time from the drop-down menu.
- End Time: Choose time from the drop-down menu. Includes a Do not restart until the next profile time value. This value extends the blackout window until the next time the deployment profile is scheduled to run.
NAVIGATION Software Management > Profiles > Alerting
The Alerts page manages Software Management patch alert profiles. Each alert profile represents a different set of alert conditions and actions taken in response to an alert. Multiple alert profiles can be assigned to an endpoint concurrently. Changes to an alert profile affect all machine IDs assigned that alert profile. Different types of machines may require different alert profiles. Alert profiles are visible to all VSA users. Alerts are processed every six hours.
Reviewing Alarms Created by Software Management Alerts
- Monitor > Alarm Summary
- Monitor > Dashboard List > any Alarm Summary Window within a dashlet
- Agent > Agent Logs > Agent Log
- The Agent > Agent Logs > Monitor Action Log: Shows the actions taken in response to an alert, whether or not an alarm was created.
- Live Connect > Asset > Log Viewer > Alarm
Actions
- New: Creates a new alert profile.
- Edit: Edit an existing alert profile. You can also double-click an alert profile to open it.
- Delete: Deletes an existing alert profile.
- Copy: Saves a selected alert profile with new name.
- Alerts Configuration: Configures the format of an alert notification message.
Summary tab
This tab sets basic options about an alert profile and how duplicate alerts are filtered.
- Name: The name of the alert profile.
- Description: A description of the alert profile.
- Merge by Patch or Merge by Machine
- Filter duplicate alerts: Prevents duplicate alerts from being generated for a specified number of time periods.
- Time Frame:
- Days
- Hours
- Minutes
- Every X days/hours/minutes: Number of days, hours, or minutes to suppress duplicate alerts.
- Time Frame:
Alert Types tab
This tab specifies the conditions that cause an Software Management alert to be created. The format for notifying users about each alert type can be changed using the Alerts Configuration button.
- New patch is available
- Patch install fails
- OS Auto Update changed: The machine user changes OS Auto Update settings.
Actions tab
This tab of an alert profile determines the actions taken in response to any of the alert types encountered by an endpoint assigned that alert profile.
- Create Alarm: If selected and an alert type is encountered, an alarm is created.
- Create Ticket: If selected and an alert condition is encountered, a ticket is created.
- Email Recipients (comma separated): If selected and an alert condition is encountered, an email is sent to the specified email addresses.
- Script Name to Run: If an alert condition is encountered, run the selected agent procedure.
- Users Notified in Info Center: If selected and an alert condition is encountered, a notification is sent to the specified user's Info Center > Inbox.
- Users Notified in Notification Bar: If selected and an alert condition is encountered, a notification is sent to the specified user's notification bar.
Endpoints tab
Lists all machines using the selected alerts profile.
- Add: Assigns the alert profile to selected machines.
- Delete: Removes an alert profile assignment from selected machines.