3rd-Party Software 2.0: VSA 9 third-party patching
NAVIGATION Software Management > Profiles > 3rd-Party Software 2.0
In the 9.5.9 release, VSA introduced the new version of the Software Management module — 2.0. The K3PP Software Catalog menu item has been renamed 3rd-Party Software 2.0.
Advantages
- Frequent module updates thanks to native in-house technology without any third-party dependencies.
- Reliable Windows patching, including BIOS and driver patching, using the native Microsoft Update service.
- Better performance and reduced storage consumption on end machines.
- A native VSA software application catalog to install, update, and uninstall third-party software.
Limitations
- Offline mode for OS patches should be configured separately using Microsoft WSUS. Refer to this Microsoft article.
- Offline mode for third-party software is not supported.
- Virus removal OS patches are not supported.
- Several third-party applications do not exist in the software catalog. Refer to VSA 9 Software Management application catalog.
Tier-based software update system
The latest versions of software are uploaded to the catalog, a process that involves verifying software integrity and ensuring compatibility. Tier-based categorization prioritizes software updates based on their importance and impact on operations.
| Tier | Description | Update Time Frame | Applications |
|---|---|---|---|
| Tier 1 | High-priority software applications essential to core business operations. They receive immediate attention and the fastest turnaround times. | 1 business day | • Google Chrome • Firefox • Microsoft Edge • Java Runtime 8 • TeamViewer • SmartFTP • Any Tier 2 or Tier 3 software update with CVSS 9.0+ * |
| Tier 2 | Standard software applications that support day-to-day activities but are not as critical as those in Tier 1. These applications are updated regularly but within a more extended time frame. | 5 business days | • 7-Zip • Acrobat Reader DC • Cisco Webex Meetings • Foxit PDF Reader • Microsoft Teams • Microsoft Office / Microsoft 365 • Jabra Direct • KeePass 2 • LastPass • Notepad++ • Skype for Business • SQL Server Management Studio • Zoom • Any Tier 3 software update with CVSS 7.0-8.9 * |
| Tier 3 | Less critical software applications for which updates are scheduled based on available resources and demand, with the longest processing times among the tiers. | 10 business days | All other software |
* FortiClient VPN updates are consistently processed within 10 business days.
Migration
During migration, you must migrate Scan and Analysis and 3rd-Party Software 1.0 profiles.
Deployment and Override profiles do not need to be migrated.
NAVIGATION Software Management > Profiles > Scan and Analysis
Scan and Analysis profiles define an OS Patches Engine and, therefore, need to be updated to support the new module version.
- Select a profile.
- Click Edit.
- The Edit Scan and Analysis Profile dialog box is displayed.
- Select Kaseya 2.0 in the OS Patches Engine field.
- Click Save to save the profile.
During the next scheduled scan procedure, VSA will use the new version of the module to perform the scan. Your override profiles will continue to analyze newly discovered patches.
NOTE Virus removal patches are not supported.
NAVIGATION Software Management > Profiles > 3rd-Party Software 2.0
NAVIGATION Software Management > Management > Machines
NOTE Software Management 2.0 introduced the 3rd-Party Software 2.0 profile, a replacement for the 3rd-Party Software 1.0 profiles.
- Create a new profile for third-party applications.
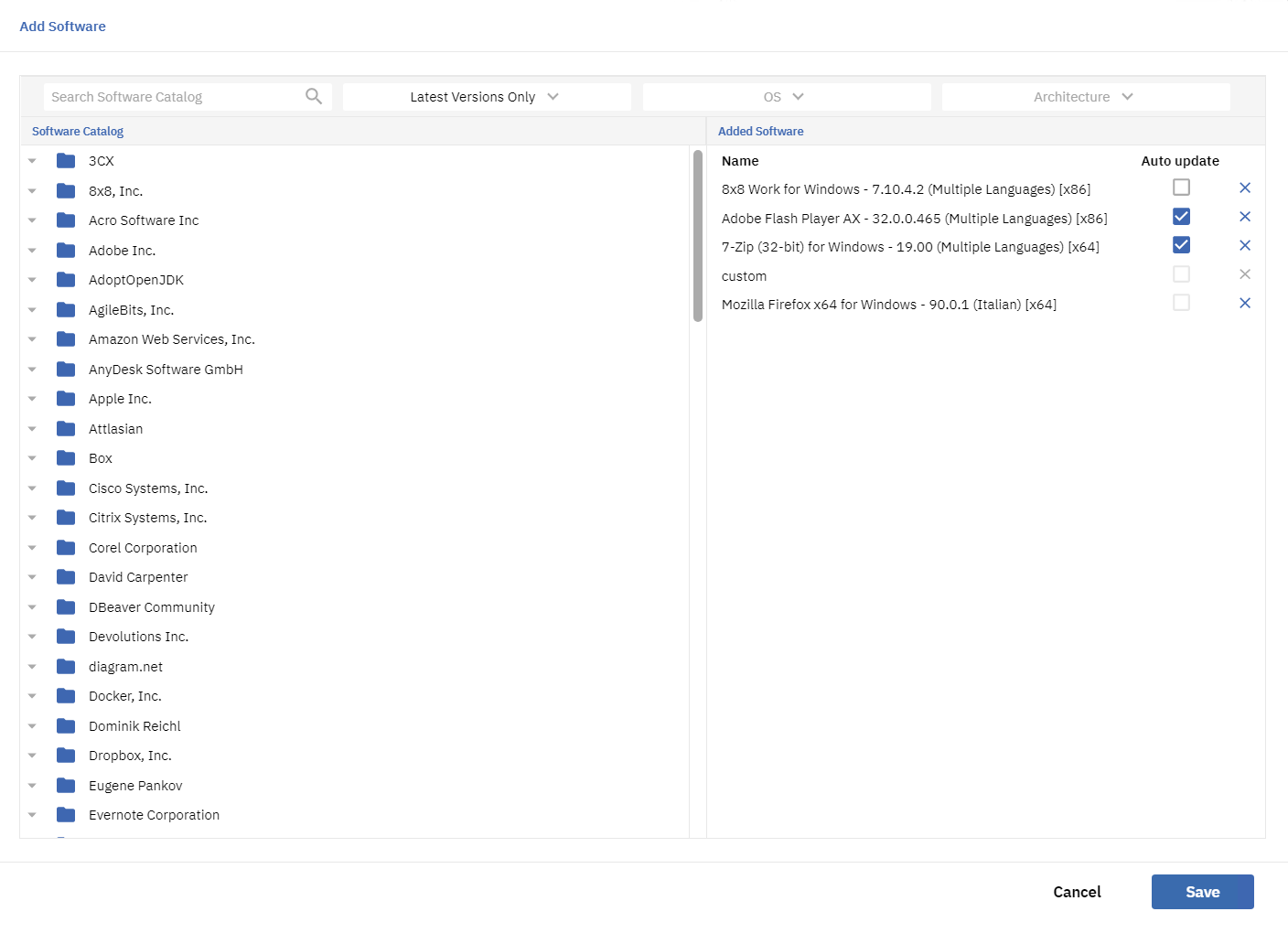
- Specify a set of applications to be installed and updated. Use the Auto update option to automatically approve new software versions.
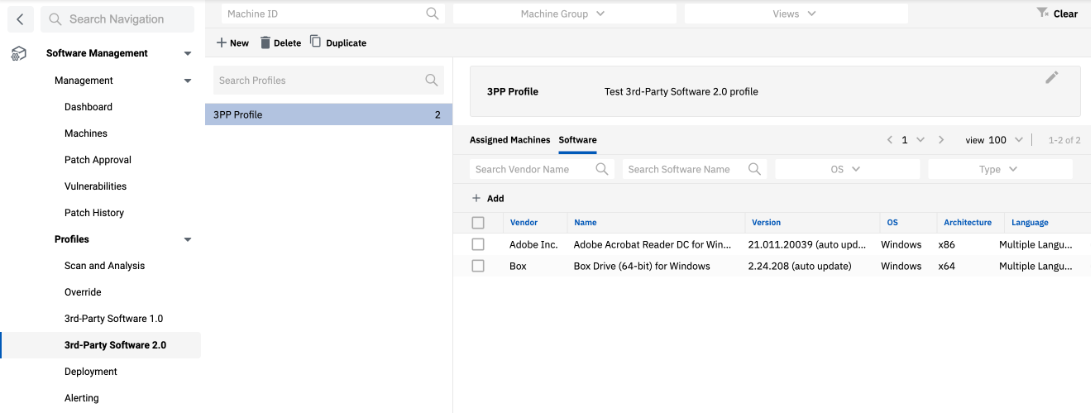
- Assign a new profile to the list of machines. Navigate to Machines. Refer to Machines.
- Reassign the 3rd-Party Software 2.0 profile to a list of machines.
- Use the Assign Profiles button and select a new 3rd-Party Software 2.0 profile in the 3rd-Party Software field. Be attentive to include the same list of machines.
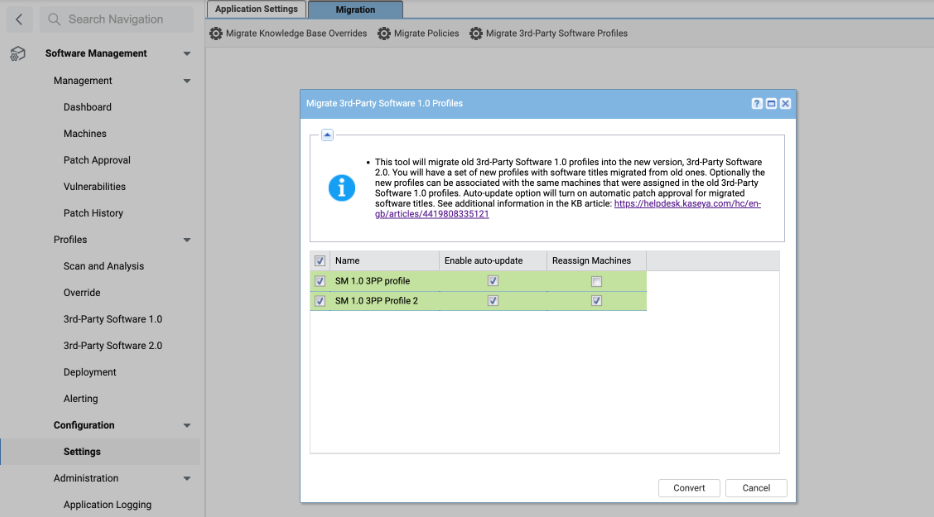
NAVIGATION Software Management > Configuration > Settings > Migration
The migration interface allows you to automatically create new profiles and reassign machines.
- Navigate to the Migration tab on the Settings page. Refer to Migration.
- Click Migrate 3rd-Party Software Profiles.
- Select the check boxes for the profiles to be migrated.
- Select the Enable auto-update check boxes to automatically approve new software versions.
- Select the Reassign Machines check boxes to automatically reassign machines to the migrated profile.
Auto update
NAVIGATION Software Management > Profiles > 3rd-Party Software 2.0 > Select Profile > Software > Add
On the Add Software page, the Auto update column is displayed in the Added Software section.
- The check box is selected when adding the latest version.
- The check box is cleared when the latest version is not added.
- The check box is cleared when the custom installer is added.
The auto-updated applications show this flag in the Version column in the format [version number] (auto update).
EXAMPLE 7.10.4.2 (auto update)
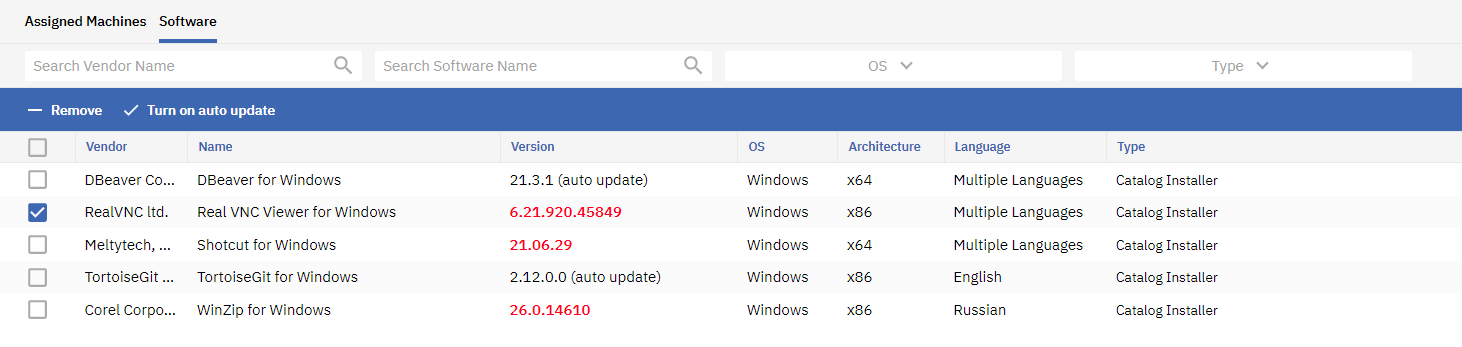
When applications are selected in the grid, the following actions are available:
- Turn on auto update
- Turn off auto update
When you click Turn off auto update and confirm the action, the specified version will be installed during deployment.
For applications with auto-update turned off, the Update action will not be displayed in the Version column.
Security update severity rating system
VSA Software Management 2.0 uses the Windows Update API to detect and install OS patches on Microsoft devices.
Microsoft breaks these updates into four severity categories: Critical, Important, Moderate, and Low.
VSA Software Management breaks these updates into two severity categories: Critical and Recommended.
| Microsoft Severity | Software Management Severity |
|---|---|
| Critical | Critical |
| Critical | Critical (Older than 30 days) |
| Important | Critical |
| Moderate | Recommended |
| Low | Recommended |
As follows is a breakdown of the four Microsoft severity categories with the corresponding VSA Software Management severity in parentheses:
A vulnerability whose exploitation could allow code execution without user interaction. These scenarios include self-propagating malware (for example, network worms) or unavoidable common use scenarios where code execution occurs without warnings or prompts. This could mean browsing a web page or opening an email.
Microsoft recommends that customers apply Critical updates immediately.
A vulnerability whose exploitation could result in compromise of the confidentiality, integrity, or availability of user data or of the integrity or availability of processing resources. These scenarios include common use scenarios where the client is compromised with warnings or prompts regardless of the prompt's provenance, quality, or usability. Sequences of user actions that do not generate prompts or warnings are also covered.
Microsoft recommends that customers apply Important updates at the earliest opportunity.
Impact of the vulnerability is mitigated to a significant degree by factors such as authentication requirements or applicability only to non-default configurations.
Microsoft recommends that customers consider applying the security update.
The impact of the vulnerability is comprehensively mitigated by the characteristics of the affected component. Microsoft recommends that customers evaluate whether to apply the security update to the affected systems.
For more information, refer to the Microsoft Security Update Severity Rating System.