Ransomware Detection
Ransomware Detection in VSA 9, part of the Endpoint Protection module, is a secure and fully featured cloud platform which provides an extra layer of security, allowing you to deploy the Ransomware engine to the endpoints. The RDM monitors for the existence of crypto ransomware on endpoints using proprietary behavioral analysis of files and alerts you when a device is infected. Once ransomware is detected, RDM can isolate the device and attempt to stop suspected ransomware processes to prevent the ransomware from spreading.
Operations
NAVIGATION Endpoint Protection > Operations > Dashboards > Ransomware Detection
The Dashboards page displays the following widgets:
Active Ransomware Detections
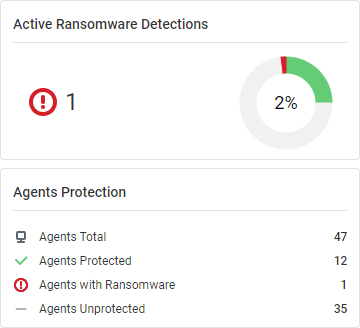
This widget displays the total number of active ransomwares detected.
Ransomware Total Detections
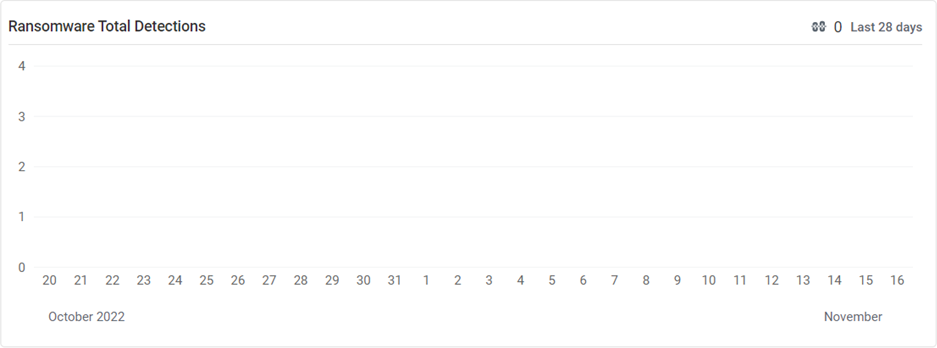
This widget displays the number of ransomware detection instances daily for the last 28 days in a graphical representation.
Agents Protection
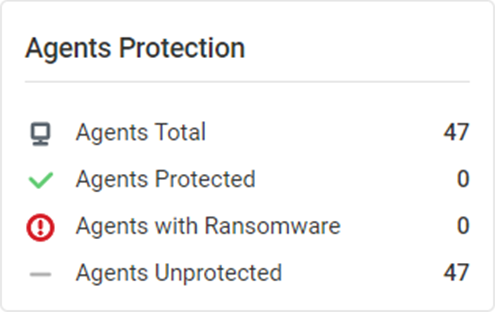
This widget displays the counts of the total number of agents, protected agents, agents with ransomware, and unprotected agents.
Alerts
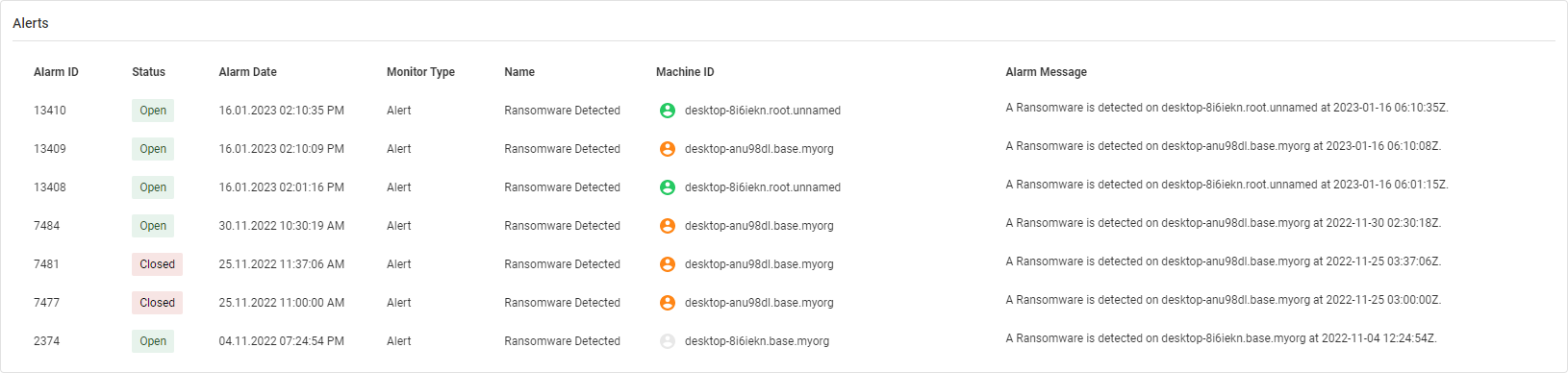
This widget displays the following information:
- Alarm ID
- Status
- Alarm Date
- Monitor Type
- Name
- Machine ID
- Alarm Message
Deployment Events
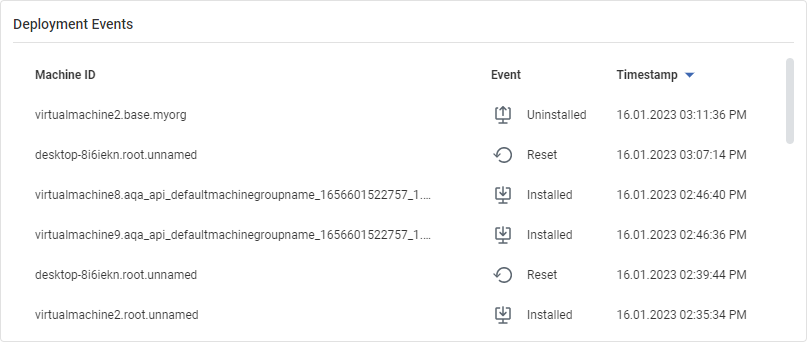
This widget displays the following information:
- Machine ID
- Event
- Timestamp
Detection Events
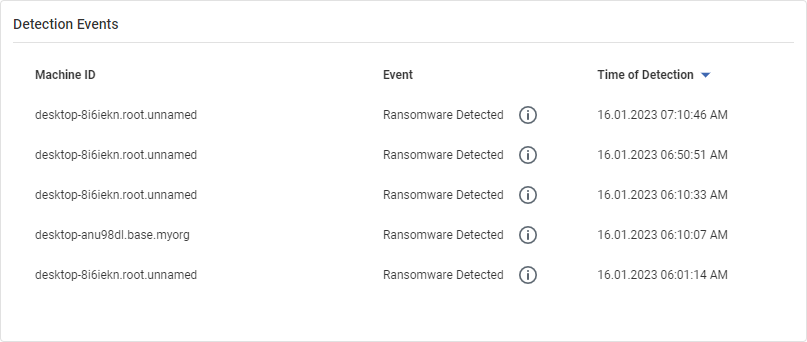
This widget displays the following information:
- Machine ID
- Event
- Time of Detection
NAVIGATION Endpoint Protection > Operations > Machines > Ransomware Detection
The Machines page enables you to select the endpoints on which Ransomware Detection can be enabled. It also provides global alerts configuration, where you can configure what happens when ransomware is detected.
EXAMPLE You can configure to automatically terminate all the processes (if running) on an endpoint in the event of ransomware detection. The alert actions enable you to configure a system to go into isolation automatically in the event of ransomware detection.
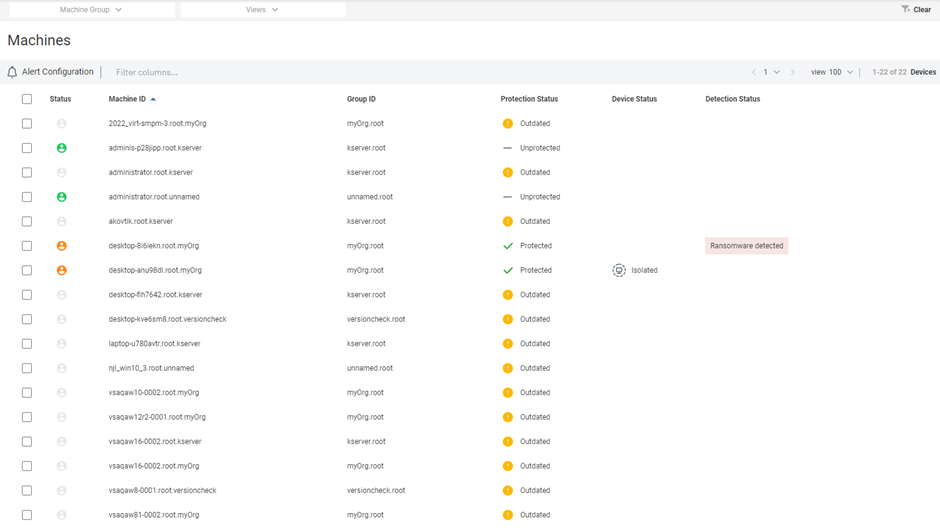
The Machines page displays the following information in a tabular format:
- Status: Hovering over the status displays the agent details.
- Machine ID
- Group ID
- Protection Status
- Protected: This status is displayed for the machines on which Ransomware Detection is installed.
- Unprotected: This status is displayed for the machines on which Ransomware Detection is not installed.
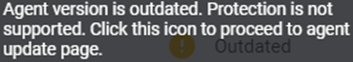
- Outdated: This status is displayed for machines on which the agent version is outdated.
- Device Status
- Isolated: This status is displayed for machines which have been isolated following ransomware detection.
- Detection Status
- Ransomware Detected: This status is displayed for the machines on which ransomware has been detected.
How to...
All machines with Device Status displayed as Unprotected are eligible for installing Ransomware Detection
NOTE The machines for which Device Status is displayed as Outdated are not eligible for installing Ransomware Detection. You must update outdated agent versions before proceeding with Ransomware Detection installation.
Perform the following steps to install Ransomware Detection:
- Select the check box for the machines on which you will install Ransomware Detection.
- The footer menu is displayed.
- Click Install.
- In the Install Ransomware Detection protection dialog box, click Install.
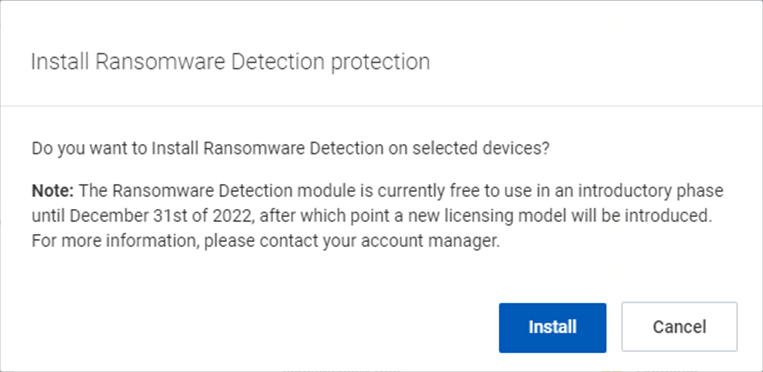
The pop-up installation confirmation message is displayed.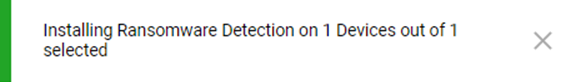
The Protection Status of the machines on which Ransomware Detection is installed will display Protected.
Perform the following steps to uninstall Ransomware Detection:
- Select the check box for the machines from which you will uninstall Ransomware Detection.
- The footer menu is displayed.
- Click Uninstall.
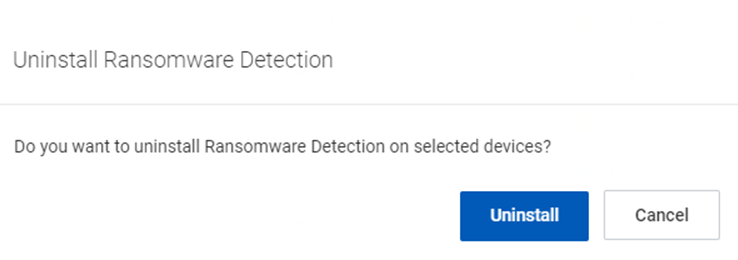
- In the Uninstall Ransomware Detection dialog box, click Uninstall.
The pop-up uninstallation confirmation message is displayed.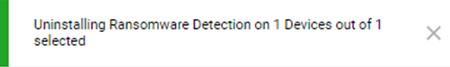
The Protection Status of the machines on which the Ransomware Detection is installed will display Unprotected.
Perform the following steps to configure alerts:
- Click Alert Configuration.
- In the Alert Configuration dialog box is displayed, select the check box corresponding to the alerts you want to configure, and click Apply.
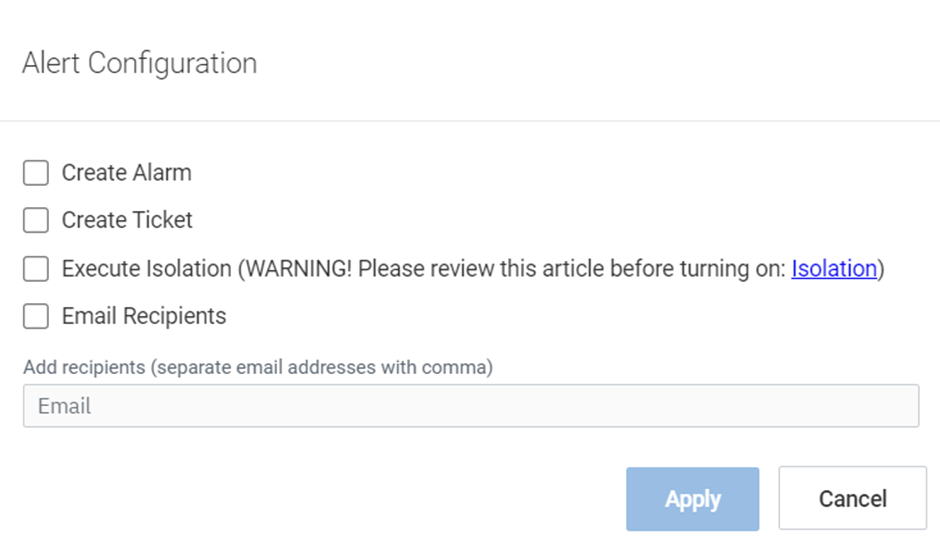
NOTE If you select the Email Recipients check box, you must enter the email addresses of the recipients in the Email field.
You can isolate a device on which ransomware is detected to prevent it from spreading.
This action will block all network connectivity from the device, except for the addresses used to connect to the VSA server.
NOTE While in isolation state, the agent will remain online in VSA, but Remote Control and Live Connect sessions will not be possible.
Perform the following steps to isolate a device:
- Select the check boxes for the machines you will isolate.
- The footer menu is displayed.
- Click Isolate.
- In the Isolate Device dialog box, click Isolate.
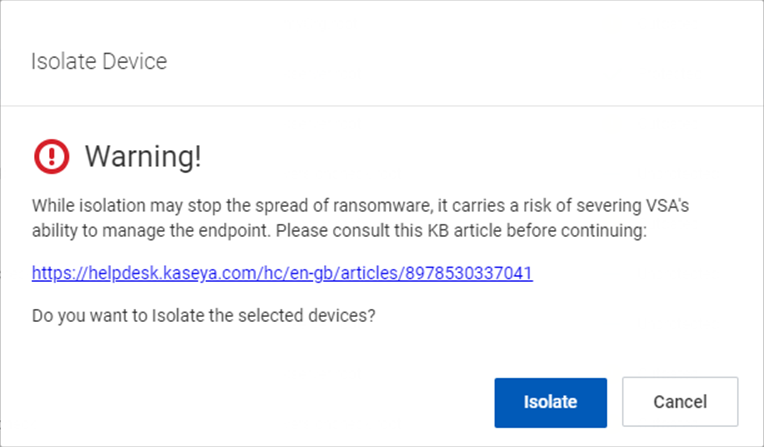
The pop-up isolation confirmation message is displayed.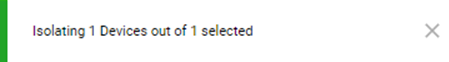
The Device Status of isolated machines displays Isolated, and the Protection Status displays Protected.
NOTE The isolated devices cannot communicate with anything on the internet or the rest of the network except for the Kaseya server.
Perform the following steps to stop isolating a device:
- Select the check boxes for the machines you will stop isolating.
- The footer menu is displayed.
- Click Stop Isolate.
- In the Stop Isolating Device dialog box is displayed, click Stop Isolating.
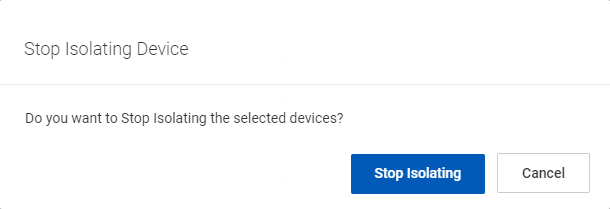
The pop-up stopping isolation confirmation message is displayed.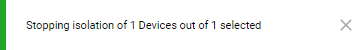
The Device Status of the machines on which isolation is stopped no longer displays Isolated, and the Protection Status displays Protected.
Ransomware Detection logging
NAVIGATION Endpoint Protection > Application > Logging
The Logging page maintains a history log of all the events associated with ransomware deployment, which includes ransomware events, event logs, and information collected from the endpoints. This information is primarily used for troubleshooting purposes.
The Logging page displays the following information in a tabular format:
- Event Date: The date on which the event occurred.
- Event Name: The name of the event.
- Machine ID: The machine that the event applies to.
- Group ID: The machine group that the event applies to.
- Message: Details of the event.
- Admin: The VSA admin who initiated the event.
Filtering columns
In the columns drop-down menu, select the column you want to filter.
The selected column is displayed in the Filter columns field.